DP Staff Incident Log
How to log and manage incidents
Incidents
The aim of the Incident Log is to provide you with a central location to manage and process both Data Breaches and Cyber-attacks through its life cycle.
Historically the GDPRiS portal only allowed users to capture information regarding data breaches, now the portal can cater for both data breaches and cyber-attacks. Since both data breaches and cyber-attacks are classed as Incidents, we have introduced a new section called “Incident Log”.
Incident typical meaning – “an action likely to lead to grave consequences”
Access the Incident Management Tool
The Incident Management Tool can be accessed via the navigation menu or via the Incident and Subject Requests widget on the school dashboard.

Overview
The Incidents and Subject Requests Overview page provides counts on the Incidents raised across a twelve-month period and the status of the Incidents.

Incident Settings
When incidents are raised, certain members of your school should be made aware so that the correct people can start to investigate and manage them. This can be done via the “Incident Settings” which can be accessed via the navigation menu down the left-hand side under “Incidents and Subject Requests”.
Response Teams
In the Incident Settings you can select your DP Lead for Data Breaches and your Team Lead for Cyber Incidents as well as their team members.

Important Note: When an incident is raised, depending on the type of incident and if you have added Leads and Team Members for data breaches and cyber incidents, those users will be notified via an email that an incident has been raised in the GDPRiS portal and will be prompted to investigate it.
If the DP Lead is the head of both groups they get notified of both breaches and cyber incidents.
If this section is not filled in, all School DP Staff users will receive an email.
If an incident is logged without the breach or cyber box ticked the notification will go to all DP leads in both the Breach and the Cyber Response Teams and then once a DP lead has ticked the relevant box only the relevant response teams will be notified.
Escalation/Reporting Information
In the Incident Settings you can add your contacts for points of escalation such as Police, Insurance and Information and Security Service providers.
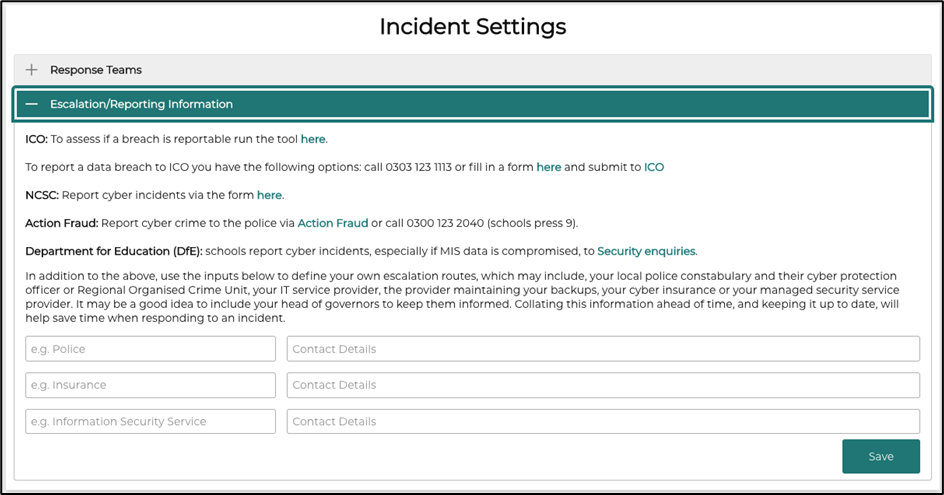
Links are provided for the ICO, NCSC (National Cyber Security Centre) incidents form and the Police for their Action Fraud forms as well as the DfE (Department for Education) for security queries.
How to log an Incident
To create a new Incident record, simply navigate to the Incident Log page by clicking on “Incidents and Subject Requests” and then “Incident Log”. You will then be able to click on “Add Incident” in the top right-hand corner of the page.

Fill in the relevant information required:
Discovered – When the Incident came to the attention of a member of staff.
Title – A rough descriptive title which identifies what the incident refers to.
Description – Describe what has happened with regards to the incident however, please refrain from adding any personal identifiable information.
Type – You can select either a Breach, a Cyber Incident or both depending on the type of Incident which you are raising. This can be left blank if you are unsure at this point.
The incident type ‘Drill’ is so schools can run through a test scenario for an Incident.
Attach Document – An option has been provided for you to attach a document if required.
Once the Incident has been created you will be shown the “Facts Card” for you to fill in, to the best of your abilities to provide as much information as you can regarding the Incident.

The purpose of the Facts Card is to provide as much information as you can as the raiser of the incident so that the appropriate members of staff can use that information in dealing with the incident.
Fill in as much information as you can and then click “Save” if you have made changes or “Close” if you simply wish to skip this page at this moment in time. You will be able to come back to the Facts Card later in the process if you choose to.
Updating an Incident
In order to update an incident, simply navigate to the Incident Log page via the navigation menu down the left-hand side of the portal and then click on the Incident Title which you would like to update.
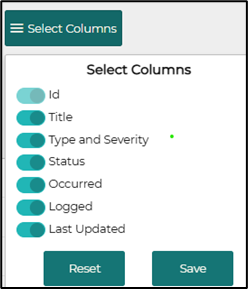
You can choose the columns that you want to see with Select Columns button
Note: If no information has been provided on the Facts Card for your Incident at the time when it was raised, you will be prompted to provide any of the required information. You can either update the Facts Card and save your changes via the “Save” button or click “Close” to not make any changes and you will be taken to the Incident.
To update the incident, click on “Update Incident”.

When you open the Update Incident window you will be provided with various options to update your incident. See screen shot for example:

Incident Status – The status is simply to provide a stage in its life-cycle which the Incident is currently in at the time.
Incident Impact – This is to show how severe the incident may impact the school
Cause – This is a long list of multiple selections to choose what contributed to or caused the incident. This is a long list of multiple selections to choose what contributed to or caused the incident. Please see Page 15 for explanation of causes
Discovered – When the incident came to the attention of a member of staff.
Breach – This is a tick box to identify that the incident is a data breach and needs to be processed in such a way.
Cyber – This is a tick box to identify that the incident is a cyber security incident and needs to be processed in such a way. Note that many breaches are also cyber incidents. An example is, ransomware wipes (personal) data on a laptop and there is no backup, then this is a breach (data lost) but also a cyber security incident (ransomware attack).
Drill - This is a tick box to identify that the incident is a so schools can run through a test scenario for an Incident.
Breach Decision – This is to document your determination of whether the data breach is reportable. This was formally the breach “Type”. (This option is only visible if “Breach” tick box is selected)
Breach Reporting Obligations Met – This tick box is to show that all data breach reporting activities have occurred for example, contacting ICO. (This option is only visible if “Breach” tick box is selected)
Threat Community – This is a multiple selection list showing who might be responsible for the incident happening.
Comment – When updating an incident, a comment is always required. Use this to document your justification for status changes.
Attachment – This provides the functionality for you to upload a document regarding the incident.
Viewable by General Staff – This is a tick box so that if the incident was raised by a General Staff user type, that user would see the update and comment which is in the update.
If this is not selected, the General Staff user who raised the incident would not see the update.
This option will only be visible if the incident was raised by a General Staff user type.
In the screen shot below, you will be able to see an updated incident with comments, an attached document and the breach decision updated.
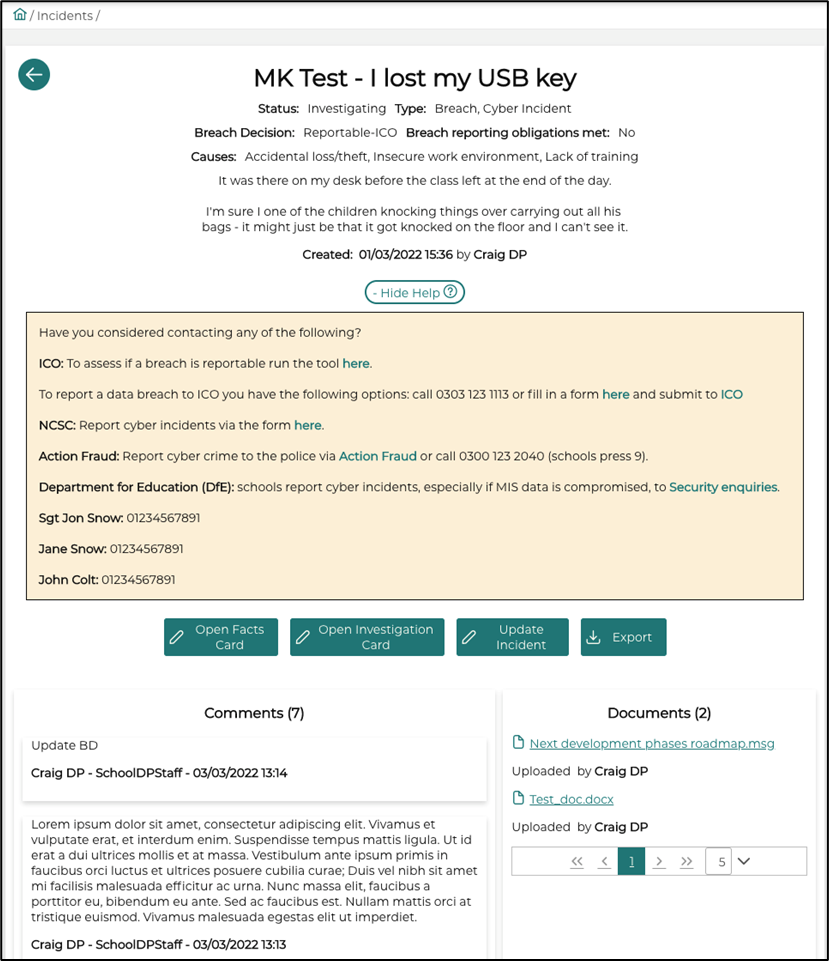
Facts Card
As previously described, the Facts Card is for information to be provided from the user who created the incident providing as much information as they can. The Facts Card can be accessed by navigating into the Incident and clicking on “Open Facts Card”. This can be updated at any point of the incident life cycle.
Investigation Card
There is a separate Investigation Card for the users who are investigating and resolving the incident in question.
The Investigation Card can be accessed by navigating into the Incident and clicking on “Open Investigation Card”. This can be updated at any point of the incident life cycle.

Helpful Information
In the different parts of the Incident Management Tool are sections of text to provide helpful information on how to fill in the relevant section you are in or what to do etc. Please refer to these if you need to.
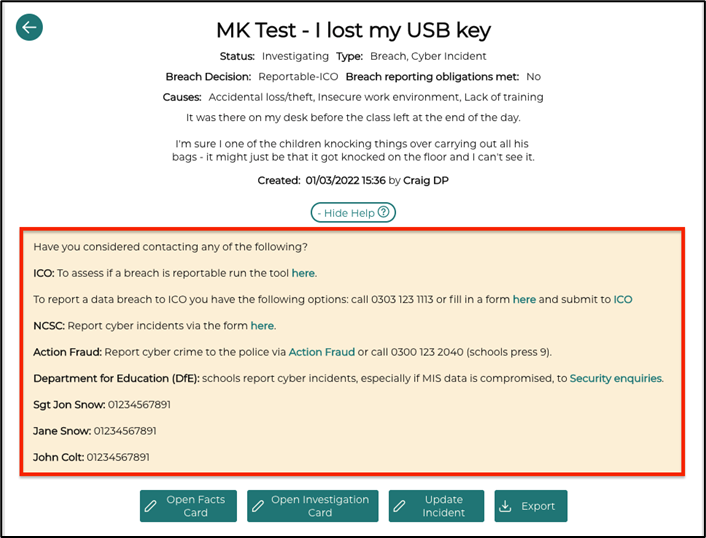
Export
We have provided the means for you to export the information from your incident to a Word document, so that it can be provided to users outside of your GDPRiS portal. Navigate to your incident which you would like to export, click on “Export”. (This will open a popup window)
You will be able to save the report to a location of your choosing.
The report provides the following information from your incident:
Incident Summary:
Organisation Name
Incident Number
Date when the incident was logged
Incident Title
Incident Description
Status
Incident Impact
Causes
Incident Type
Date when the Incident was discovered
Breach Decision
Breach Obligations Met
Comments
Answers from the Facts Card
Answers from the Investigation Card
|
(Distributed) Denial of Service |
Explanation |
|
Accidental loss/theft |
Most typically this is the loss or theft of either a device such as a laptop or a mobile phone, or of hardcopy data (e.g. paper files). Even if the data is encrypted, the event is still an incident, albeit probably less severe. |
|
Adversary-in-the-Middle |
Also called man-in-the-middle attack: this is where an attacker intercepts traffic and is able to either read, or even alter its contents. |
|
Brute force |
If an attacker has access to a data repository (e.g. via a login form), they can try to make thousands of attempts at guessing the password. Lists of common passwords and some reconnaissance on their victims help with this type of attack. |
|
Data exfiltration |
This is a type of data loss event, where you discover that data has intentionally ro accidentally been leaked to outside the confines of your control and to unauthorised recipients. |
|
Excessive data held |
If you hold too much data, or you hold data for longer than is necessary to meet the purpose of your processing activity, this is a breach of your data protection policy and a breach of the law. |
|
Hacking (session hijacking, injection attacks, keyloggers, ..) |
A broad class of events, where malicious individuals attempt to misuse your information resources in an attempt to compromise them. The skill level of hackers, aswell as their motivation can vary widely (e.g. protest, personal gain, thrill). The methods and the results of hacking also vary widely. |
|
Inadequate contract |
If processing activity is not covered by a contract, that gives both parties of the contract sufficient protection, or the data subjects. |
|
Inadequate policy |
Policy can refer to a written document, instructing your workforce how to behave. It can also refer to a technical control that enforces certain behaviour. |
|
Inappropriate disposal |
After the period of usefulness ends for data it needs to be disposed of. Disposal is inappropriate if the data can be recovered. |
|
Inappropriate handling |
Inappropriate handling usually refers to a violation of data safeguards. Examples could be: unauthorised members of staff or other bodies were involved, careless sharing or diclosing of documents. |
|
Insecure work environment |
Where the work environment is such, that unauthorised individuals can easily get access to information, e.g. by eavesdropping on conversations or by overlooking computer screens. Or indeed, physical measures such as doors or locks are not sufficiently strong. |
|
Lack of training |
Lack of awareness and skill often result in incidents |
|
Malware or Ransomware |
Malware and a special type of malware called Ransomware are very often spread via emails, and unsuspecting members of staff will infect first their machine and then their co-workers' machines. Malware infections are at least disruptive, but can easily cause severe incidents and data breaches. |
|
Misconfiguration |
Misconfigured computers are open to a wide variety of forms of attacks. It is good practice to apply consistent and strong security settings to all computers. |
|
Misdirected communication |
One of the most common forms of data breach is when email accidentally includes inintended recipients. |
|
Negligence |
Staff who are not fully aware of or willingly choose to ignore policy. |
|
No/weak encryption |
Encryption and good key management are good ways to protect information. The absense of either puts data at risk of breach. |
|
Phishing |
Phishing emails - cleverly worded emails to prompt recipients into disclosing secrets or making payments. |
|
Processing not in line with rights |
Under data protection law, data subjects enjoy a number of rights. If an organisation is not able or willing to satisfy those rights, they are breaking the law. |
|
Social engineering |
Malicious activities using human interaction, usually employing psychological manipulation. |
|
Supply chain attack (vendor compromise) |
An attack on an organisation by first attacking and compromising less secure entities in the supply chain. |
|
Trojan |
A Trojan is malware, packaged and installed as part of legitimate looking software. |
|
Unintended disclosure of sensitive data |
Sensitive data (esp also personal data) that get into the hands of unauthorised recipients. |
|
Unlawful processing |
Processing of personal data, that is taking place either without or with dubious lawful basis, or otherwise contravenes the GDPR. |
|
Unpatched systems |
Malware and hackers often go after unpatched systems. |
|
Unsolicited marketing |
Sending marketing information without the necessary consent (opt-in) according to Privacy and Electroniic Communications Regulation (PECR). |
|
Violation of Acceptable Use Policy (AUP) |
The Acceptable Use Policy - if defined - instructs your staff what they can and can't do with the data and computer systems of your school. |
|
Weak/Compromised credentials |
Hackers make attempts at guessing weak passwords. Even in the absense of an actual compromise, weak credentials (e.g. the use of shared or common passwords) is a security incident. |
![GDPRiS-new-black (2).png]](https://kb.gdpris.co.uk/hs-fs/hubfs/Images/GDPRiS%20Logo%20Images/GDPRiS-new-black%20(2).png?width=113&height=85&name=GDPRiS-new-black%20(2).png)